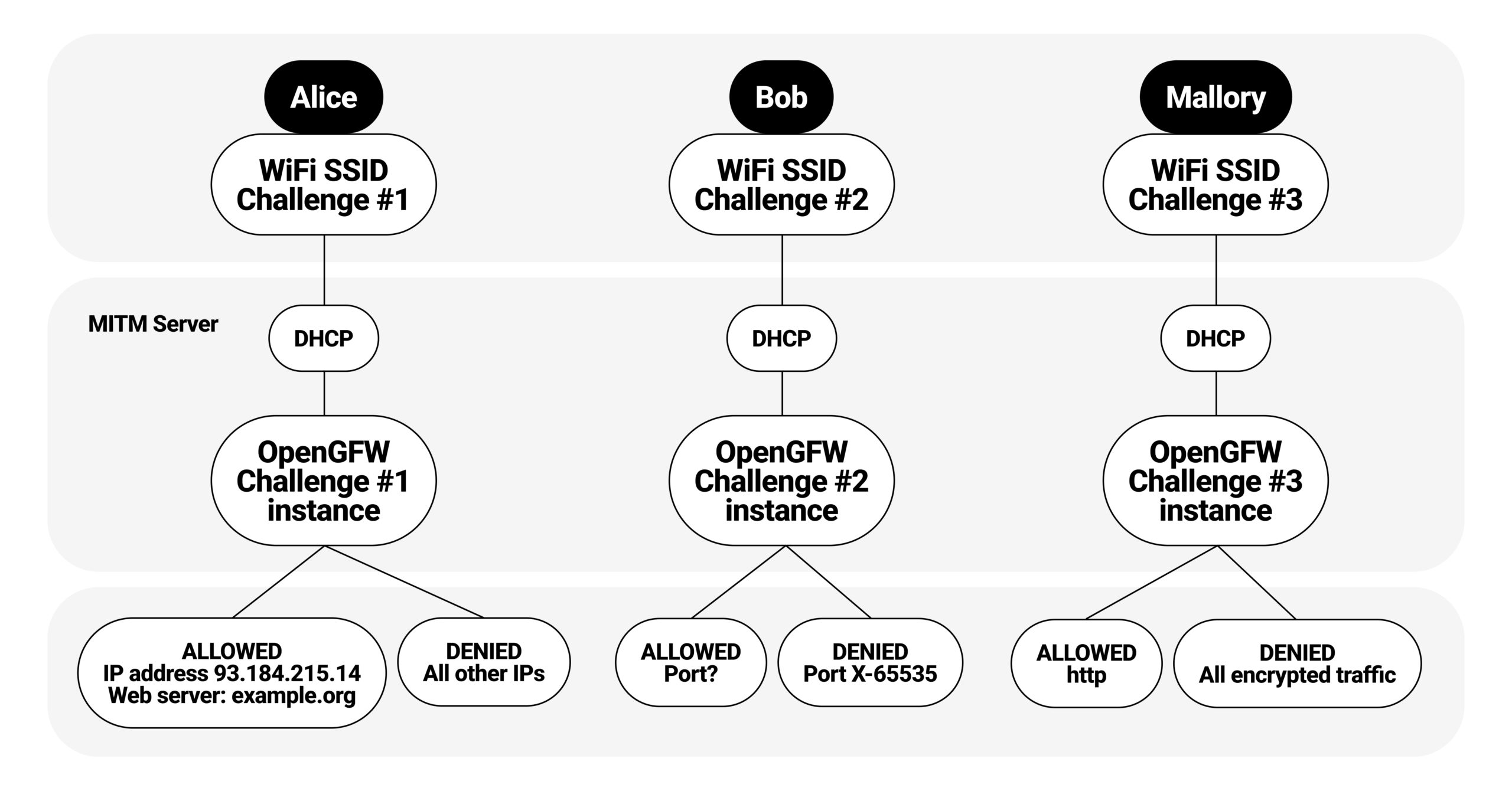
The Blockathon is a unique, hands-on experience for technologists and practitioners to test and refine their skills in circumventing internet censorship and shutdowns. Built for those ready to face real-world challenges, the Blockathon offers a controlled network environment that simulates various restrictions, from basic filtering to deep packet inspection and protocol blocking. Powered by the OpenGFW project and adapted by eQualitie, this virtual setup recreates the intense conditions found in restrictive regions, pushing participants to innovate and discover new solutions.
Originally developed to provide a realistic testing space, the Blockathon allows participants to fine-tune circumvention tools and reveal vulnerabilities in a safe setting before these tools reach the field. Participants from previous events have uncovered real solutions—like DNS tunneling through port 53 with OpenVPN or leveraging the Iodine library—that have made meaningful impacts on keeping communications open and secure worldwide.
Challenges
Easy Mode: Light filtering and basic restrictions. (ssid: blockathon 1)
Encrypted Traffic Blocking Mode: Defeating advanced censorship of encrypted protocols. (ssid: blockathon 2)
Mystery Challenge: Unknown restrictions unveiled during the event.Challenges (ssid: blockathon 3)
Airplane Mode: Testing in a near-complete offline environment. (ssid: blockathon 4)
RightsCon special: Break out of the Runet (ssid: blockathong RU)
Past events
… one of the participants had figured out that since example.org was resolving in the browser — it meant DNS was also running (port 53, protocol UDP).
This escape route from the Splinternet was discovered during the Brussels conference
They tunneled an OpenVPN connection over port 53 and were able to connect to a server and get out! Another participant used a similar strategy with the Iodine library.
Code of Practice
As we work to develop tools to bypass censorship, we must also recognise the dual-use nature of this technology. Circumvention tools designed to empower people can sometimes be repurposed by the very censors we aim to counter.
At the Blockathon, we emphasise the importance of behaving responsibly and ethically when creating technology. Participants are expected to consider the potential for misuse and take appropriate measures to mitigate those risks. Whether it’s building better encryption tools or traffic obfuscation methods, we must remain aware of how these technologies could be used by adversaries and ensure that our work supports the preservation of privacy and security for vulnerable populations.
